It feels like every other day, we read a news headline about another data breach or cyber attack. Large and small businesses alike, from any industry, are vulnerable. You know that protecting your company’s data is critical, especially when it comes to sharing that data with others, but navigating ever-changing security guidelines can be confusing. How can you ensure that your suppliers, vendors, and partners are committed to keeping your data secure?
One way to check whether a company’s systems are designed to protect your data is to ask for their SOC 2 Type II report. SOC, or System and Organization Controls, is a set of security standards created by the American Institute of Certified Public Accountants (AICPA). There isn’t a checklist of specific SOC requirements to meet. Instead, it’s up to each company to design their own systems and policies for protecting their users’ data.
During a SOC audit, an independent CPA firm reviews the organization’s internal controls and determines whether they meet the SOC standards. Then the organization can share the final audit report with current or potential customers, partners, etc. to build trust in their systems and handling of data.
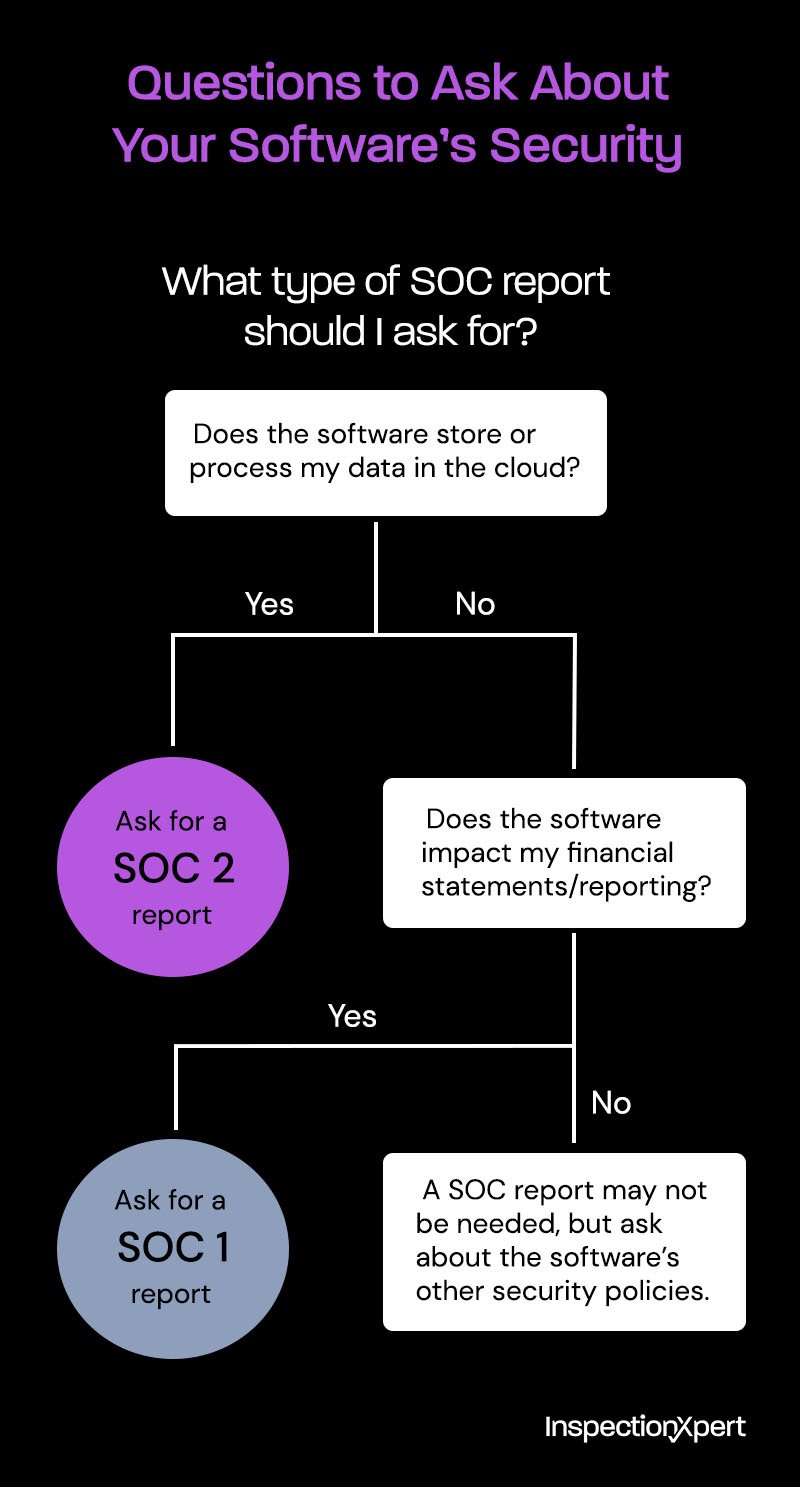
There are different types and levels of SOC reports, each covering a different scope or set of standards. We’ll focus on SOC 2 Type II in this article, but here’s a quick overview of each type.
There are also a couple of newer types of SOC reports introduced in the past few years: SOC for Cybersecurity and SOC for Supply Chain. These are more specific to cybersecurity and supply chain risk management policies, and include overlap with SOC 2 criteria.
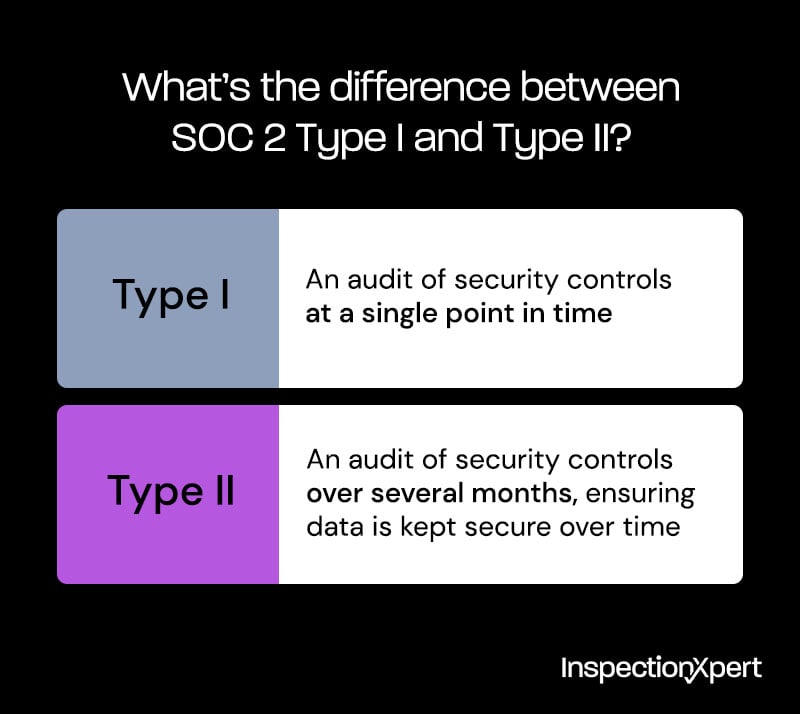
A SOC 2 Type II report attests that an organization’s internal controls have been audited over time to prove that they are designed and operating effectively to keep user data secure.
SOC 2 is designed for service organizations from any industry that store customer data in the cloud: data hosting or processing, cloud storage, Software as a Service (SaaS) companies, etc.
SOC 2 Type II is the most comprehensive of the SOC reports because it tests the functionality of an organization’s security systems and other controls over a longer period of time, often several months. Type I reports only review the design of the controls at one point in time, so they can’t actually demonstrate that the controls are working as intended over time.
To allow companies to develop systems that fit their unique processes and risks, SOC 2 doesn’t include a list of specific requirements to meet. Instead, SOC 2 includes general criteria for protecting customer data called the Trust Services Principles, which are used as guidelines for evaluating and reporting on the organization’s controls:
Organizations undergoing SOC 2 audits are required to cover the Security principle in their report, which shows that they have implemented thorough data protection policies such as intrusion detection, network or application firewalls, multi-factor authentication, etc. From there, the organization chooses which of the other Trust Services Principles to include in its SOC 2 audit, depending on which ones are relevant to their business. Throughout the exam period, the auditor reviews and tests the organization’s systems to make sure they are designed and working properly to meet the chosen SOC 2 principles.
This is the typical process for organizations going through a SOC 2 audit:
The outcome of a SOC 2 Type II exam is the auditor’s report. The report includes descriptions of the organization’s systems, processes, and controls for addressing security and the other Trust Services Principles. It also includes the auditor’s opinion about the controls’ design and functionality.
Ideally, the auditor’s opinion will state that the organization’s controls are suitably designed and operating effectively over the period of time they were examined (this is sometimes called an “unqualified” or “unmodified” opinion). A less ideal scenario would be if the auditor finds a few things out of place (such as missing or misleading information, or a process not working as intended), or worse, that there are pervasive issues with the controls.
If all goes well, the organization can share their clean SOC 2 report with current or potential customers, partners, etc, to answer questions about their security measures and how user data is handled.
With the increasing number of hacks and data breaches we’re seeing today, it’s more important than ever to ensure your company’s data is protected. Checking whether the vendors, suppliers, and other companies you share your data with have gone through a SOC 2 Type II audit can help mitigate these risks. While a clean SOC 2 Type II report isn’t a guarantee that your data will never be compromised, it’s an assurance that the organization has comprehensive security measures in place to keep your data protected.
If you work with defense-related items or data, you may need to follow ITAR security requirements. Learn more about ITAR and get a free compliance checklist.
Copyright 2025 InspectionXpert Corporation, is a wholly owned subsidiary of Ideagen Inc, All Rights Reserved